As part of a vulnerability research project for our WordPress Security Scanner at WPcans.com, we have been auditing popular WordPress plugins looking for security issues.
While auditing the WordPress plugin Loginizer, we discovered a SQL Injection vulnerability and a Cross-Site Request Forgery (CSRF).
This plugin is currently installed on 500,000+ websites.
About the plugin
According to WordPress.org:
Loginizer is a WordPress plugin which helps you fight against bruteforce attack by blocking login for the IP after it reaches maximum retries allowed. You can blacklist or whitelist IPs for login using Loginizer. You can use various other features like Two Factor Auth, reCAPTCHA, PasswordLess Login, etc. to improve security of your website.
Are You at Risk?
This vulnerability is caused by the lack of sanitization in user provided data and missing checks. As soon as possible upgrade to the latest version of the plugin: 1.3.6.
You can also use our free security scanner at WPScans.com to scan for this vulnerability or the open-source tool wpscan.
Technical Details CSRF
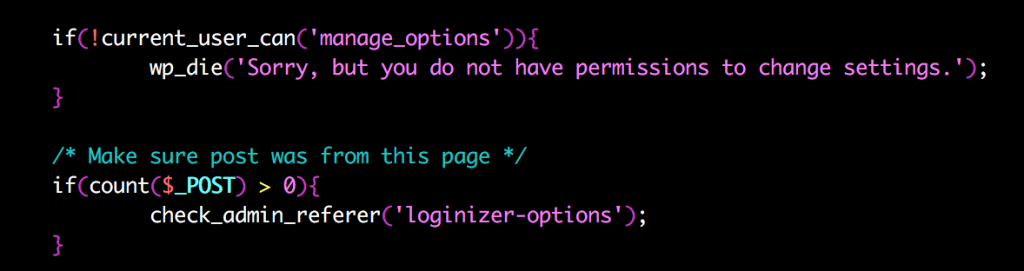
First, the CSRF vulnerability can be triggered when a admin or a user with manage_option privileges clicks a link provided by an attacker. The link can be hidden with a URL-shortener for example, screenshots from the broken referer/nonce check:
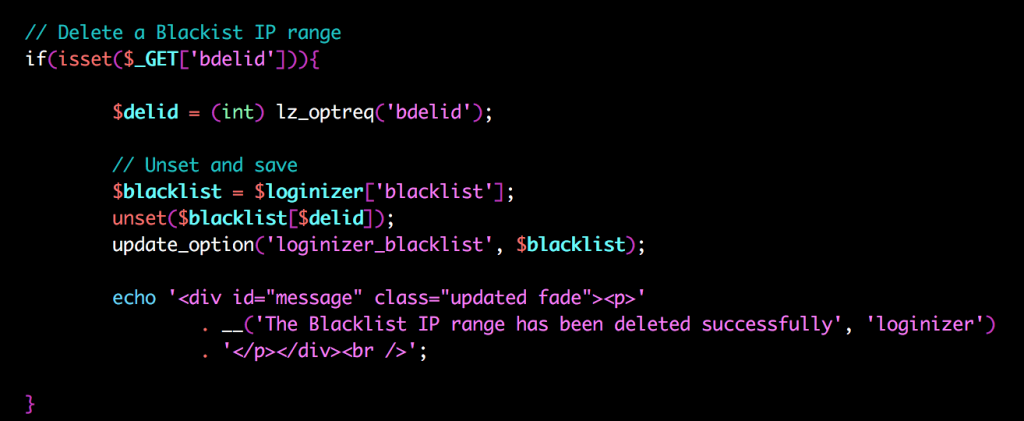
As the above screenshot shows the check_admin_referer() function is only executed if $_POST is set. But deleting a whitelist or blacklist IP does not require POST, only GET:
Technical Details SQL Injection
When someone tries to login at least one SQL-query is executed by the plugin. The query looks something like this:
SELECT * FROM `wp_loginizer_logs` WHERE `ip` = 'myip...
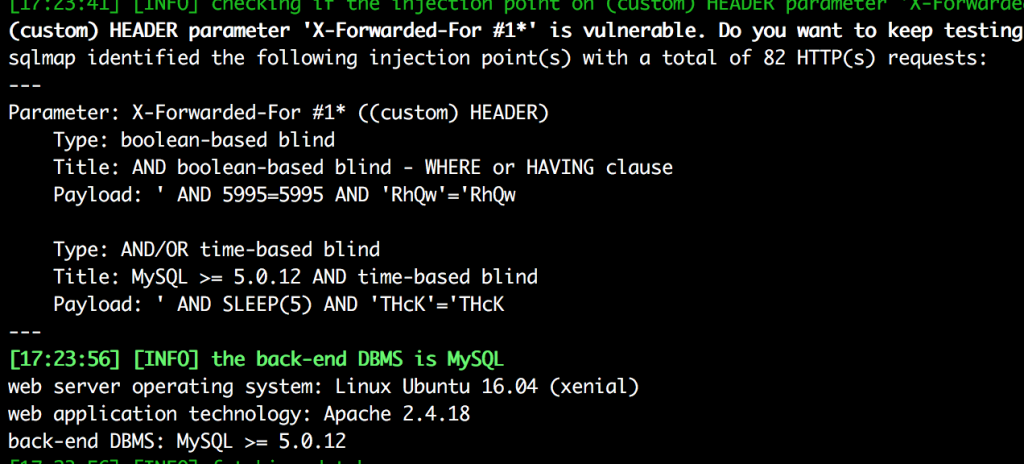
The problem above is that an attacker can set IP using different http-headers such as X-Forwarded-For depending on the server setup. This http-header is forwarded without any sanitization to lz_selectquery() and then $wpdb->get_results().
This is a blind SQL injection vulnerability and can be exploited using sqlmap, as example:
Timeline
- 2017-08-02 Vulnerabilities found
- 2017-08-04 Plugin vendor contacted using online form
- 2017-08-07 Fixed by vendor: WordPress.org changelog
- 2017-08-07 CVE ID requested
- 2017-08-08 Blog post published
CVE ID:s assigned from Mitre:
- CVE-2017-12650
- CVE-2017-12651
Vulnerabilities found by Jonas Lejon.


Pingback: Loginizer Plugin Gets Forced Security Update for Vulnerabilities Affecting 1 Million Users – WordPress Tavern
Pingback: Loginizer Plugin Will get Compelled Safety Replace for Vulnerabilities Affecting 1 Million Customers - #NewsEverything #WordPress | WordPress Blog
Pingback: Loginizer Plugin Gets Forced Security Update for Vulnerabilities Affecting 1 Million Users - WP Epitome
Pingback: Loginizer Plugin Gets Forced Security Update for Vulnerabilities Affecting 1 Million Users - TechNonStop
Pingback: Loginizer Plugin Gets Forced Security Update for Vulnerabilities Affecting 1 Million Users | WordPress | WooCommerce | Web Site | fabbrica42
Pingback: Le plugin Loginizer obtient une mise à jour de sécurité forcée pour les vulnérabilités affectant 1 million d'utilisateurs - WordPress Tavern | Script-News
Pingback: Loginizer插件针对影响100万用户的漏洞获取强制性安全更新 - WP建站
Pingback: Loginizer Plugin Gets Forced Security Update for Vulnerabilities Affecting 1 Million Users
Pingback: CVE-2020-27615: SQL Injection Vulnerability in WordPress Loginizer Plugin Affected Over One Million Sites – TerabitWeb Blog
Pingback: The Loginizer plugin gets a forced security update for vulnerabilities affecting 1 million users – WordPress Tavern – blogger dz
Pingback: البرنامج المساعد لوجينيزر يحصل على تحديث أمني إجباري لنقاط الضعف التي تؤثر على مليون مستخدم – WordPress Tavern – blogger dz – بولجر ديزاد
Pingback: Loginizer Plugin Gets Forced Security Update for Vulnerabilities Affecting 1 Million Users – Clevity
Pingback: Loginizer Plugin Gets Forced Security Update for Vulnerabilities Affecting 1 Million Users - wordpress-450839-1562426.cloudwaysapps.com
Pingback: CVE-2020-27615: SQL Injection Vulnerability in WordPress Loginizer Plugin Affected Over One Million Sites – Unified Networking
Pingback: WordPress Vulnerabilities: Top 4 Security Threats in 2021- WPSec