From time to time we do forensic investigations of WordPress breakins. When we do the investigation there is often one or more backdoors placed in the filesystem or modified legit WordPress-related files in wp-includes, themes or plugins.
This is not only related to WordPress but all sites running PHP such as Drupal, Magento etc.
Finding backdoors in the filesystem can be time consuming and doing checksum checking is not always possible. So I wanted to find out how good antivirus software are these days to find PHP and WordPress backdoors.
On my personal Gist Github I have collected more than 10 different backdoors found on real breakins and forensic investigations.
Test 1 – VirusTotal
The Google owned VirusTotal.com service allows you to upload suspected malware and find out how many different antivirus-engines detecting the malware. So I uploaded the 10 different backdoors and here is the result:
- Backdoor 1 – Detected by AVware as BPX.Shell.PHP
- Backdoor 2 – No detections
- Backdoor 3 – Detected by GData as Script.Backdoor.Perger.A
- Backdoor 4 – No detections
- Backdoor 5 – No detections
- Backdoor 6 – No detections
- Backdoor 7 – Two detections Nod32 PHP/Agent.GA and Fortinet PHP/Agent.GA!tr
- Backdoor 8 – DrWeb PHP.Mailer.26
- Backdoor 9 – Bkav VUL26C0.Webshell
- Malware 10 – 7 engines detected this file as malicious
Test 2 – Indicators of Compromise
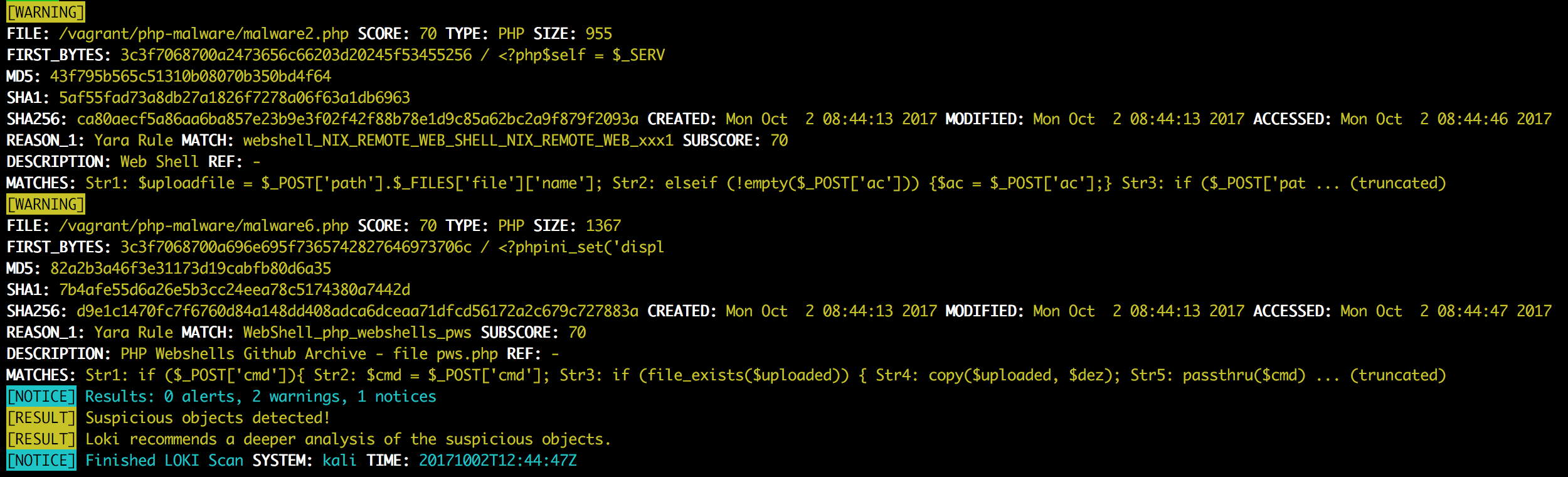
- Backdoor 1 – Big_Numbers1
- Backdoor 2 – webshell_NIX_REMOTE_WEB_SHELL_NIX_REMOTE_WEB_xxx1
- Backdoor 5 – Big_Numbers1
- Backdoor 6 – WebShell_php_webshells_pws
- Backdoor 7 – Big_Numbers1
- Backdoor 8 – network_smtp_raw
- Backdoor 8 – possible_includes_base64_packed_functions
- Backdoor 8 – with_images
- Backdoor 8 – with_urls
- Backdoor 8 – without_attachments
- Backdoor 9 – Big_Numbers1
- Backdoor 9 – php_uname
- Backdoor 10 – function_through_object
- Backdoor 10 – php_malfunctions
- Backdoor 10 – php_uname
- Backdoor 10 – possible_includes_base64_packed_functions
Wow. That looks good, but what about false positives? By looking at the alerts there should be lots of files triggering in the WordPress-core as example. When I did a scan on a plain WordPress installation with yara I’ve got 48 alerts and 0 with Loki.
Test 3 – Findbot
Findbot.pl is a simple Perl-script to find suspicious web files such as PHP-shells and backdoors. It was created in 2013 by CBL (Abuseat.org / Spamhaus).
The result from findbot is the following:
- Backdoor 1 – Suspicious(base64_decode): serialize(base64_decode(substr($o
- Backdoor 6 – Suspicious(passthru): passthru($cmd);
- Backdoor 7 – Suspicious(fsockopen): n_exists(‘fsockopen’)) {
- Backdoor 8 – Suspicious(fsockopen): g back to fsockopen”,
- Backdoor 10 – Suspicious(base64_decode): echo exe(base64_decode($_GP[‘cmd
And when it comes to false positives using findbot it finds 19 suspicious indicators in a plain WordPress installation.
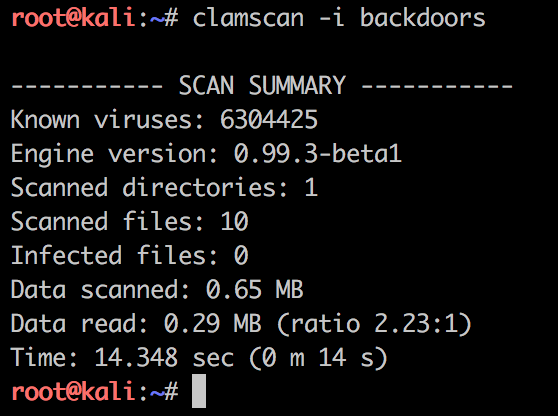
Test 4 – ClamAV antivirus
Clam AntiVirus (ClamAV) is a free, cross-platform and open-source antivirus software toolkit able to detect many types of malicious software, including PHP-shells, backdoors and viruses. In the past i’ve seen detections with clamav.
But this time there was zero detections:
Conclusions
Using yara, findbot and Loki may yield a lot of false positives and generates a lot of manual work. But when it comes to finding backdoors it is worth the time. I would recommend using the above tools together with classic forensic work such as looking at timestamps, accessed files in webserver logs, post-data and checksums.
As always, don’t forget to scan your WordPress site using WPSec.com.
Test files can be downloaded here (password: malware):
More backdoors can be found here: https://gist.github.com/jonaslejon


Correct. There remains no single method of identifying malware within a website. Human eyeballs are still required. This is why the scanners used by web host and some automated malware cleanup companies are at best partial solutions to full cleaning and securing a hacked website.
Can’t tell you how many times this past year I’ve been drawn into reviewing the work done by automated malware cleanup services only to find the sites harboring “eyeball” obvious back door and malicious files.
That looks good, but what about false posivites? By looking at the alerts there should be lots of files triggering in the WordPress-core as example.
I had more success with ClamAV since I added PHP malware signatures, I downloaded these from https://malware.expert/signatures/ (I am not affiliated to this site).
My ClamAV output for your files:
./malware2.php: OK
./malware6.php: OK
./malware10.php: {multi}Malware.Expert.wget.curl.lwp-download.exec.system.signature.UNOFFICIAL FOUND
./malware7.php: {HEX}Malware.Expert.PHP.SESSION.PHP.0.UNOFFICIAL FOUND
./malware8.php: OK
./malware3.php: {HEX}Malware.Expert.generic.preg.replace.post.3.UNOFFICIAL FOUND
./malware4.php: {HEX}Malware.Expert.generic.cookie.8.UNOFFICIAL FOUND
./malware5.php: OK
./malware9.php: OK
./malware1.php: OK
———– SCAN SUMMARY ———–
Known viruses: 6469743
Engine version: 0.99.4
Scanned directories: 1
Scanned files: 10
Infected files: 4
Data scanned: 0.38 MB
Data read: 0.29 MB (ratio 1.29:1)
Time: 16.550 sec (0 m 16 s)
Also, we can use Exploit Scanner, but before applying it we must know that base64 and eval codes are also used in plugins. So sometimes it will return a lot of false positives. If we don’t know about the plugin in deep then it is really hard for you to know which code is out of its place in the thousands of lines of code.
Also, we can use Exploit Scanner, but before applying it we must know that base64 and eval codes are also used in plugins. So sometimes it will return a lot of false positives.
Pingback: Is it a virus or Not? ImunifyAV found malware in analog/cache file - Robert's Technology Blog
Pingback: WordPress Forensic Investigations: Unveiling the Digital Clues - WPSec