Nmap is one our favorite tool when it comes to security testing (except for WPSec.com). Nmap was created in 1997 by Gordon Lyon aka Fyodor. The current version 7.60 contains about 580 different NSE-scripts (Nmap Scripting Engine) used for different security checks or information gathering and about six of them are related to WordPress.
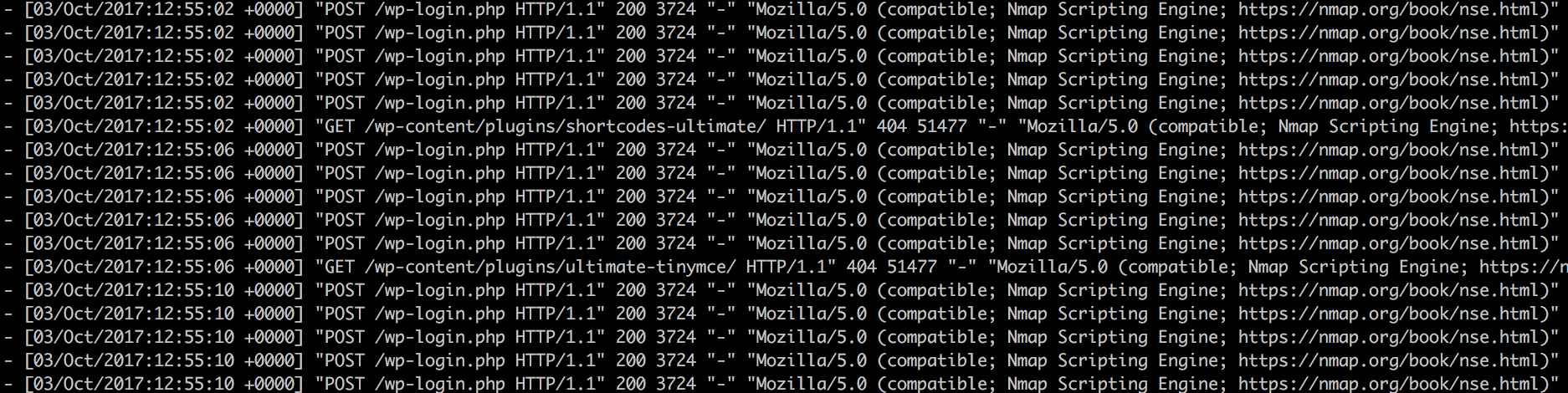
Our first test is to just use the default options in nmap and see which ports that are open:
Btw, we are using the amazing penetration testing Kali Linux distro. The above screenshot shows that there is a webserver, ssh server and MySQL listening on the network. Exposing MySQL to the network is not really safe, it’s not the target this time.
The following Nmap NSE scripts are directly related to WordPress:
- http-wordpress-users.nse
- http-wordpress-enum.nse
- http-wordpress-brute.nse
- http-vuln-cve2017-1001000.nse
- http-vuln-cve2014-8877.nse
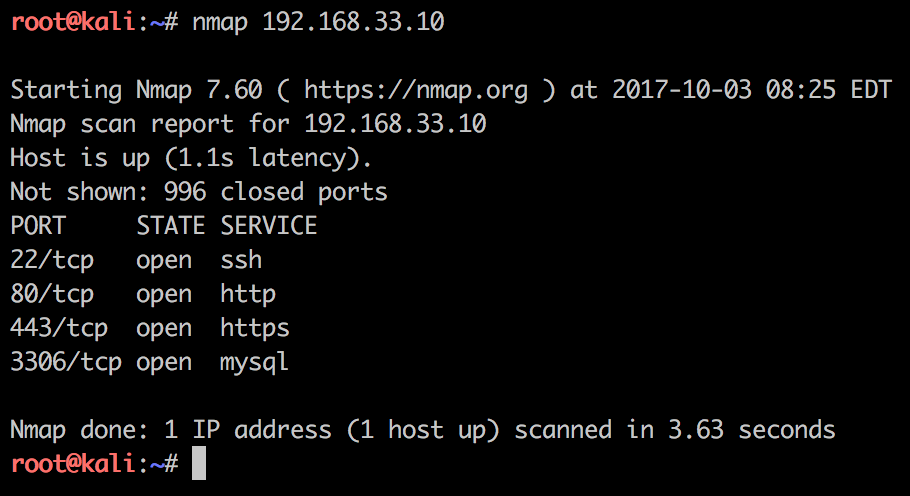
When we are running our second test we focus on the webserver and using the -A argument to Nmap to enable script scanning:
From the above screenshot we notice that the http-generator script displays the WordPress version, and in this case 4.8.2.
Now it’s time for the heavy lifting stuff: Running the WordPress scripts. We can start them by adding the
--script
argument like below. Be are that this can take some time to finish, in our test case it took about 12 minutes:
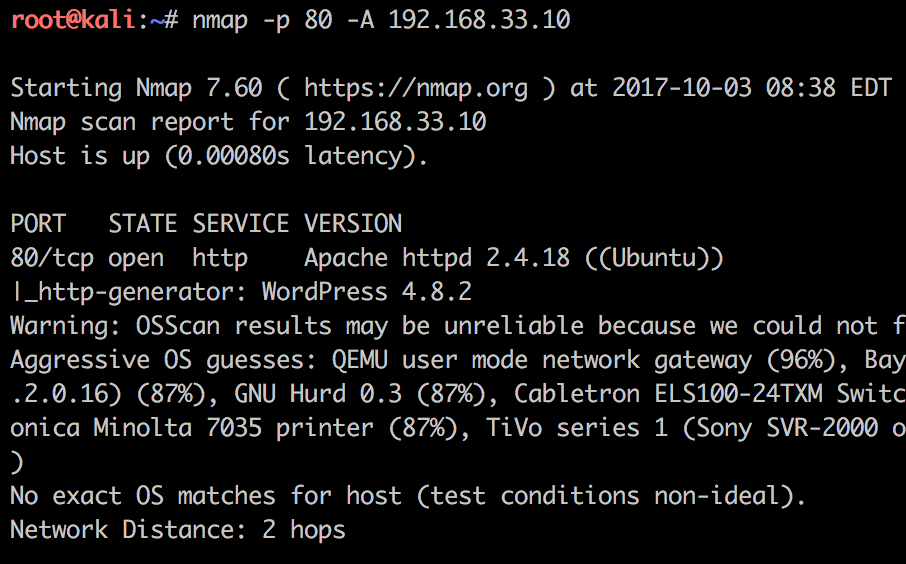
Now we’re talking! This looks cool, lets interpret the results Nmap identified. Three different themes and nine different plugins with the corresponding versions. We can also read that only top 100 themes/plugins are searched for in the http-wordpress-enum plugin.
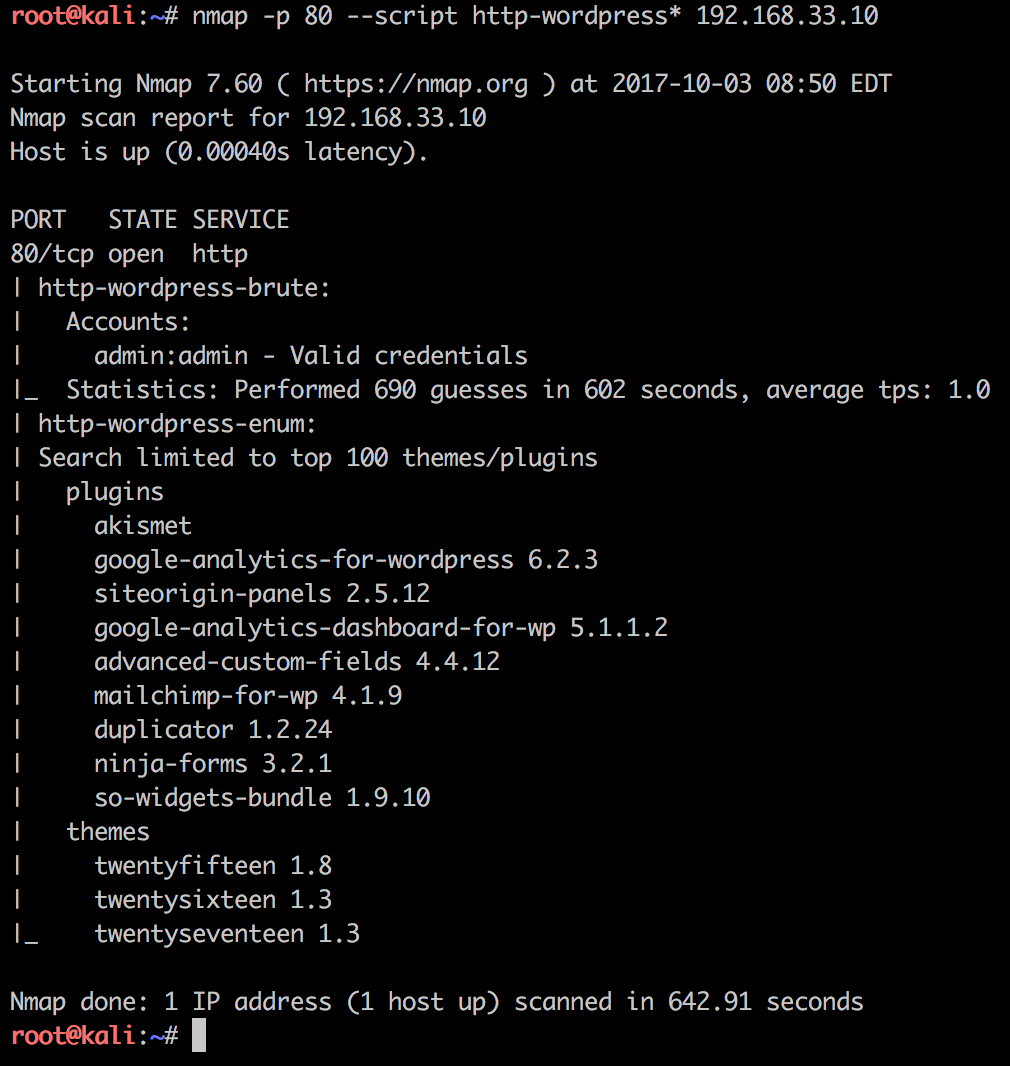
This type of bruteforce scan is very noisy and the target webserver log files looks something like this:
We can adjust the timings with -T5 argument to run a slower scan. And to change the User-Agent that telling our scanned host that we are running Nmap can be changed like this:
--script-args http.useragent="Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/40.0.2214.85 Safari/537.36"
Further we can change the number of plugins or themes to check using the following arguments:
--script-args search-limit=5000
Also we can also adjust to only enumerate for themes:
--script-args type="themes"
In our installation of Nmap with Kali Linux, Nmap can check for 4778 themes and 50553 plugins:
$ wc -l /usr/share/nmap/nselib/data/wp-themes.lst 4778 /usr/share/nmap/nselib/data/wp-themes.lst $ wc -l /usr/share/nmap/nselib/data/wp-plugins.lst 50553 /usr/share/nmap/nselib/data/wp-plugins.lst
Finally I would like to adress the login bruteforcer. As the screenshot above we can see that the NSE script http-wordpress-brute.nse found out that login admin has the password admin.
The bruteforcer also has some arguments to use:
--script-args 'userdb=users.txt,passdb=passwds.txt,http-wordpress-brute.hostname=domain.com, http-wordpress-brute.threads=3,brute.firstonly=true' <target>
As you can see the arguments are pretty self explaining, you can set threads, user-list to use and password database.
If you are looking for a large password or user-list I would recommend SecLists on Github: